26+ cisco network drawing tool
Migration from ICCM ticketing tool to Service Now SNOW 25. The increasingly sophisticated threats made by outside nation-states to the supply chains and infrastructure on which we all rely demand new defenses in software development.

Cisco Network Diagram Network Organization Chart Computer Network Cisco Networking Networking
A look at four more upgrades to the crypto network.
. The vertical cable manager finger duct with cover is 6-ft. Get secure massively scalable cloud storage for your data apps and workloads. Sc Information Technology University of Mumbai India.
Tripp Lites SmartRack SRCABLEDUCTVRT helps eliminate cable stress by organizing the cables within the SmartRack enclosure or open rack cabinet. SOLARWINDS NEXT-GENERATION BUILD SYSTEM Were setting the new standard in secure software development. Now next and beyond.
Create any diagram in just a few clicks. Many years ago when Adobe bought Macromedia they acquired a tool called Fireworks. 091 m sections to allow for multiple installation options.
Rotavirus A the most common species causes more than 90 per cent of human infectionsRotavirus is transmitted by the faecaloral routeIt infects cells that line the small intestine and produces. After a security monitoring tool identifies a malware attachment entering the network what is the benefit of performing a retrospective analysis. Stack Exchange network consists of 182 QA communities including Stack Overflow.
For example if the local on-premises network has a 1921681024 address space and one of the virtual networks has a 1050016 address space then we would need an access list entry from the local network to the virtual network which we typically would have already setup and another access list entry from the 1050016 virtual network. Use the crypto key generate rsa global configuration mode command to enable the SSH server on the switch and generate an RSA key pair. Migration from Office 2007 to Office 2013 globally 26.
Tracking need-to-know trends at the intersection of business and technology. Cisco recommends a minimum modulus size of 1024 bits. Central network security policy and route management for globally distributed software-defined perimeters.
Rotavirus is a genus of double-stranded RNA virus and the leading cause of severe diarrhoea among infants and young children nearly all of whom have an infection by age five. Sale Ends in 12 Hours. Fireworks was cheap powerful and hugely ahead of its time.
A computer network is a set of computers sharing resources located on or provided by network nodesThe computers use common communication protocols over digital interconnections to communicate with each other. Sale Ends in 12 Hours. Answered Mar 10 2017 at 1505.
A retrospective analysis can help in tracking the behavior of the malware from the identification point forward. We would like to show you a description here but the site wont allow us. SUMMIT Palm Desert.
DevOps tool integrations. 183 m high and split into two 3-ft. Drive faster more efficient decision making by drawing deeper insights from your analytics.
Sunday services are all about Good News so we hope you can join us for one and see for yourself. Analysis of Functional Neuro Images AFNI Scientific and Statistical Computing Core SSCC National Institute of Mental Health NIMH TRM Mgmt Group. 3639 10 10 gold badges 26 26 silver badges 36 36 bronze badges.
Generate RSA key pairs. When generating RSA keys the administrator is prompted to enter a modulus length. SRCABLEDUCTVRT offers toolless button mounting.
These interconnections are made up of telecommunication network technologies based on physically wired optical and wireless radio-frequency. Flowcharts org charts UML ERD network diagrams UI more You can save Gliffy Diagrams in JPEG and PNG formats and add them to Google Docs presentations wikis or webpages. Free Shipping 17 Rosewill Wireless Earbuds with Fast Charging Case Bluetooth Headphones with built-in Microphone LED Battery Indicator 4 Hours of Continuous Playtime - RW-T52.
You may need to tweak the line drawing setting as well but it is probably not likely. Hussein Kanji hkanji. It can identify how the malware originally entered the network.
11 1 1 bronze badge. Generating an RSA key pair automatically enables SSH. The Gliffy diagramming App is easy to use and even WORKS OFFLINE.
Youll find shapes to create. Migration from Blackberry BES Server to Airwatch MDM. Configuring Network Firewall Ports which are needed for SCCM server client communication.
All of our worship services include powerful music practical teaching and preaching from the Bible as well as opportunities for prayer and response and time to build relationships with other people. Save 78 1499.
2
2

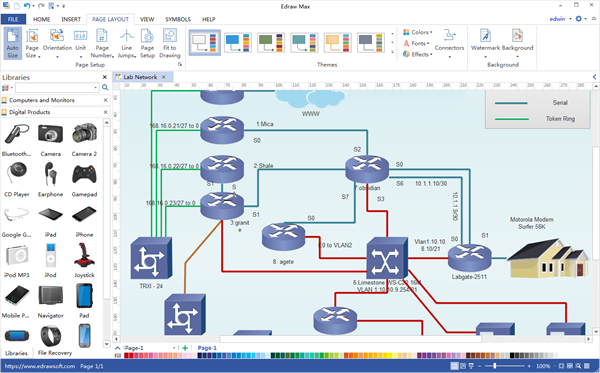
There Are Number Of Examples That Are Included With The New Cisco Networks Diagram Solution Located In The Concep Networking Network Solutions Cisco Networking
7 Network Diagram Software For Windows Mac Downloadcloud
2
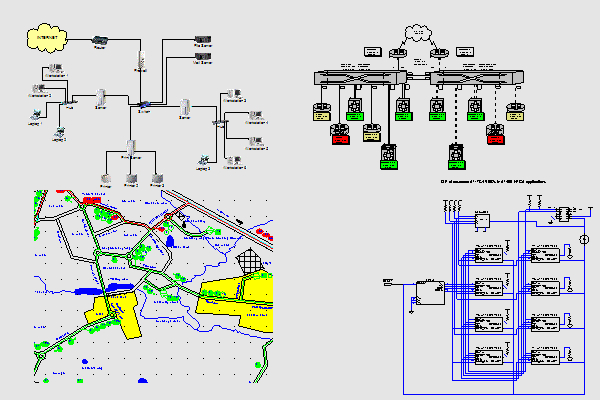
7 Network Diagram Software For Windows Mac Downloadcloud
2

Cisco Network Diagram Roaming Wireless Local Area Network Diagram Cisco Networking Computer Network Local Area Network
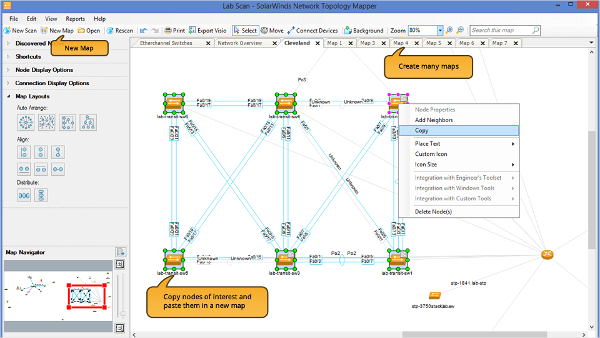
7 Network Diagram Software For Windows Mac Downloadcloud

Network Diagram Guide Learn How To Draw Network Diagrams Like A Pro Networking Best Vpn Virtual Private Network

Computer Network Architecture Computer And Network Examples Computer Network Network Solutions Cisco Networking Technology

Cisco Logical Network Diagram Networking Cisco Networking Cisco
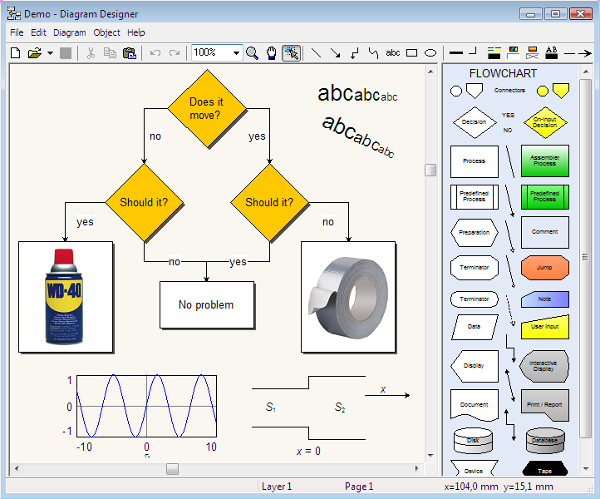
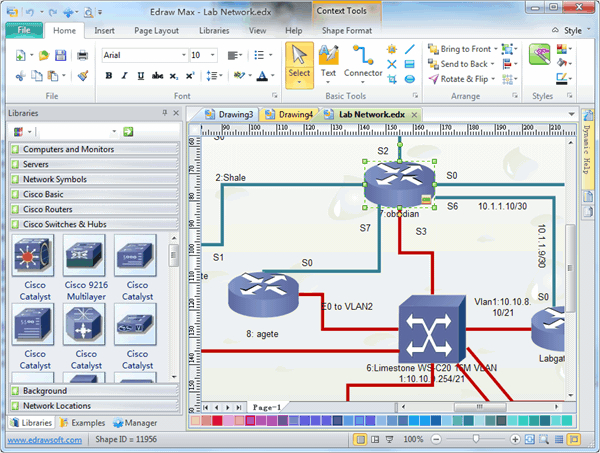
7 Network Diagram Software For Windows Mac Downloadcloud

7 Network Diagram Software For Windows Mac Downloadcloud

Cisco Isg Topology Diagram Cisco Networking Technology Cisco Networking Network Infrastructure

Computer Network Diagram Cloud Computing Technology Computer Network Cloud Computing Services

Cisco Network Topology Diagram Cisco Networking Cisco Networking